Table of Contents
Credentials/Passwords
ITFlow allows you to store asset/URL credentials
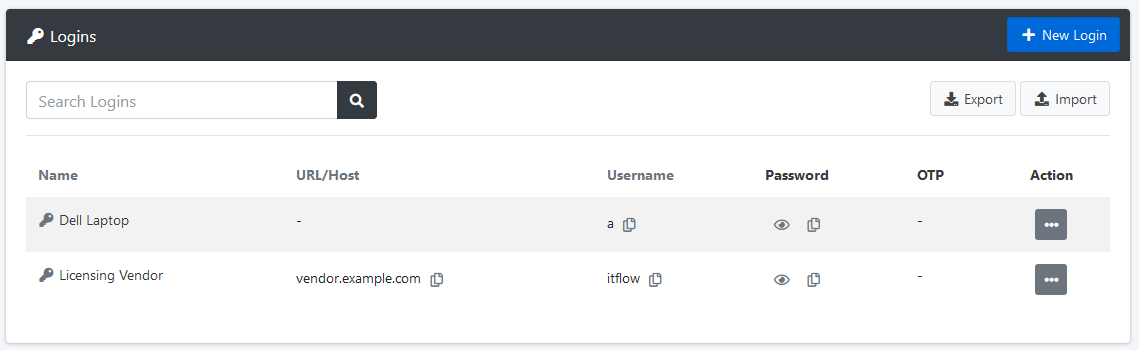
Credential Fields
- Name/Desc
- Username (encrypted in database)
- Password (encrypted in database)
- OTP
- URL
- Related vendor/asset/software
- Notes
How logins are protected
All login password data is encrypted at rest, and ideally in transit as you're using HTTPS to access your ITFlow instance, right?
In order to understand how ITFlow encrypts login entries, you must first understand the requirements:
- Securely protect login entries with encryption
- Never store the plaintext encryption key in the database / on disk
- Allow multiple users to easily and quickly access login passwords
- Not require a server TPM chip or third party server/service for secret management
With that in mind, the solution decided upon was to generate an AES master key during the initial installation and encrypt this master key for each technician using their password hash as their “user-specific key”. Each login entry is protected with this master key using AES 128-bit encryption. This ensures that each user has access to passwords without storing the plaintext master key anywhere. In order to avoid storing the user's password or the master key for the duration of their session, an encrypted session key is generated and stored in the users session and provided to them as a cookie. This helps to further protect the master key as it never hits the disk/database in cleartext.
This approach is by no means perfect. It also means that if you forget/lose all user account passwords and haven't backed up the master AES key, your login passwords are not able to be decrypted by anyone! We would much rather that you lose access to systems and spend the day resetting passwords than your passwords being compromised due to a server misconfiguration/compromise, etc. Make sure to backup your AES master key, and ideally have at least two admin accounts for safety.
I've abstracted some of the details here for readability. If you'd like to get into the technical detail of how this is done, please review the associated PR, specifically functions.php. If you have any questions/comments please raise them on the Forum.
(Not in active use) ITFlow Login Helper Browser Extension
A browser extension is available for Chrome. Upon being clicked, the extension will check the current site hostname and will attempt to fill the username/password of an ITFlow login entry with that hostname. Note that the extension is in Beta.